Three Ways to Better Protect Your Business from Zero Day Threats
A zero-day threat or vulnerability is one which presents itself to developers with zero-days notice for them to deliver a patch to mitigate it.

Recently, Microsoft experienced such an event which was seemingly unprecedented in scale, affecting 60,000 victims, many of which were small to medium businesses with flaws in their security. The attack was unusual in that it involved an automated threat which could attack large multiples of organisations simultaneously.
This attack was the latest in a long line of high profile cyber security hacks that are disturbingly becoming more and more frequent in nature. WannaCry, SolarWinds, TeslaCrypt are all names we’re more than familiar with that have caused serious damage and disruption to businesses around the globe.
Last week’s well-published, Microsoft zero-day attack was equally disruptive, causing businesses yet again to be extremely vulnerable until patches and fixes were able to be applied.
The primary issue here was that if businesses were completely up to date with their patches they could quickly apply the fixes from Microsoft to secure themselves, but sadly, most businesses were not.
Unpatched vulnerabilities are now responsible for 60% of cyber breaches.
Until Microsoft was able to release a single mitigation tool that worked in all environments (not just up to date ones), which came over a week later, organisations were frantically trying get on track with the patches they’d already missed before they could mitigate the threat.
We can’t stress enough how important it is to have a proactive patch maintenance strategy in place. It’s not sexy or shiny or exciting. Frankly, it’s pretty boring, but correct housekeeping with regard to patches can help avoid endless problems. We 100% recommend that all businesses have maintenance, upkeep and continuous review of patches built into their standard operations. It’s something that our engineers are fixated on with our customers because, with a consistent approach, it’s the easiest and simplest way to remove vulnerabilities. Get patch savvy and give your business the protection it needs.
Make Like a hacker. Scour every last bit of your estate for vulnerabilities.
Understand your asset inventory and then make sure that every aspect of it is correctly maintained. No this isn’t low hanging-fruit as such because the asset inventory itself can take time, but it is a hassle well worth it if you want to take your security seriously.
So many businesses we meet don’t have a full handle on their legacy applications or systems etc leaving them unprotected. These gaps are tiny little doors into your big, business-critical assets that you need to get rid of or protect.
If your network is 99% protected, it’s unprotected. It’s exploitable.
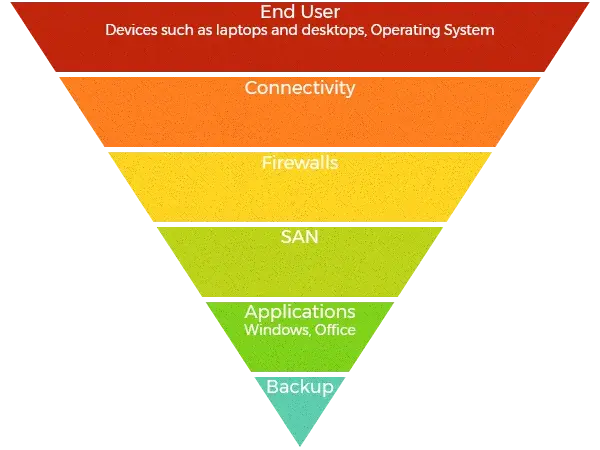
Businesses often fixate on windows updates, but they need to be updating and maintaining patches on the full stack of applications including, firewalls, switching, connectivity, back-up solutions, infrastructure, virtual machines and end-user devices. Hackers are expert at finding vulnerabilities.
This is even more relevant now that data shows that a third of workers in the UK may be staying at home. The end-user is more vulnerable in a myriad of ways due to a mix of personally owned equipment and human error. Protect every last access point to your estate and get it done quickly.
Push it through the ranks and make it everyone’s problem.
An approach that we have been using for some time whenever we spot a vulnerability within a customer’s business is to make sure that everyone right up to the c-suite is aware of it and understands it needs to be resolved. Rather than being no one in particular’s problem, the vulnerability is suddenly everyone’s issue (which of course it definitely will be if it becomes exposed to threat). Often, patches are left unapplied due to operational silos so we’ve found that if areas of vulnerability are continually exposed, discussed and shouted about in meetings, they get resolved quicker.
Delayed patching hurts your customers, employees, brand reputation and profits.
Yes, it’s a drag, but it’s still better than scrabbling around updating old patches when an automated threat, like Microsoft’s one last week, is attacking your business. Patching is probably a bad title for the task in-hand. It’s a word we don’t assign any time-critical importance to. Many businesses would perhaps fair better if we referred to the vulnerability a delayed patch update creates – a gaping hole in your IT security that needs to be filled at speed.
